Mildly Infuriating
Home to all things "Mildly Infuriating" Not infuriating, not enraging. Mildly Infuriating. All posts should reflect that.
I want my day mildly ruined, not completely ruined. Please remember to refrain from reposting old content. If you post a post from reddit it is good practice to include a link and credit the OP. I'm not about stealing content!
It's just good to get something in this website for casual viewing whilst refreshing original content is added overtime.
Rules:
1. Be Respectful
Refrain from using harmful language pertaining to a protected characteristic: e.g. race, gender, sexuality, disability or religion.
Refrain from being argumentative when responding or commenting to posts/replies. Personal attacks are not welcome here.
...
2. No Illegal Content
Content that violates the law. Any post/comment found to be in breach of common law will be removed and given to the authorities if required.
That means: -No promoting violence/threats against any individuals
-No CSA content or Revenge Porn
-No sharing private/personal information (Doxxing)
...
3. No Spam
Posting the same post, no matter the intent is against the rules.
-If you have posted content, please refrain from re-posting said content within this community.
-Do not spam posts with intent to harass, annoy, bully, advertise, scam or harm this community.
-No posting Scams/Advertisements/Phishing Links/IP Grabbers
-No Bots, Bots will be banned from the community.
...
4. No Porn/Explicit
Content
-Do not post explicit content. Lemmy.World is not the instance for NSFW content.
-Do not post Gore or Shock Content.
...
5. No Enciting Harassment,
Brigading, Doxxing or Witch Hunts
-Do not Brigade other Communities
-No calls to action against other communities/users within Lemmy or outside of Lemmy.
-No Witch Hunts against users/communities.
-No content that harasses members within or outside of the community.
...
6. NSFW should be behind NSFW tags.
-Content that is NSFW should be behind NSFW tags.
-Content that might be distressing should be kept behind NSFW tags.
...
7. Content should match the theme of this community.
-Content should be Mildly infuriating.
-At this time we permit content that is infuriating until an infuriating community is made available.
...
8. Reposting of Reddit content is permitted, try to credit the OC.
-Please consider crediting the OC when reposting content. A name of the user or a link to the original post is sufficient.
...
...
Also check out:
Partnered Communities:
Reach out to LillianVS for inclusion on the sidebar.
All communities included on the sidebar are to be made in compliance with the instance rules.
view the rest of the comments
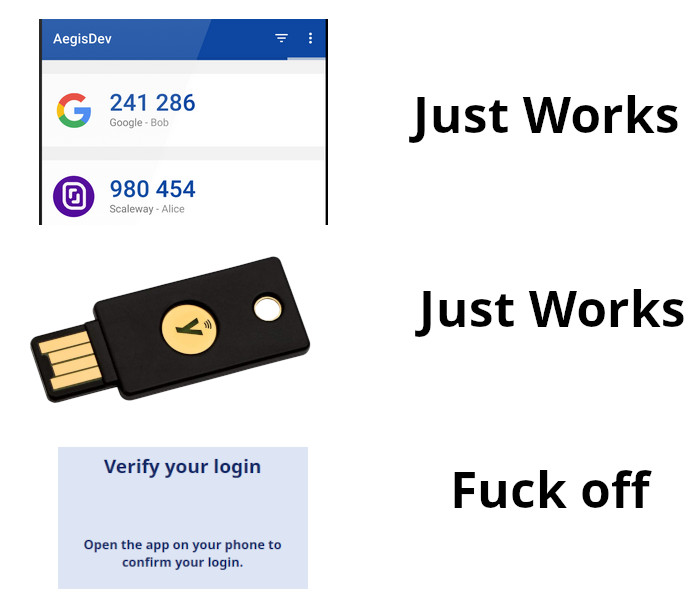
Wait, can you eli5 why multifactor authentication (MFA) (and maybe also 2-factor authentication apps) is “fuck off” levels?
Is it privacy concerns or something bigger like more points of failure for overall security? Or smaller like not every one has/wants a smart phone?
If I read it correctly the "fuck off" level refers to some proprietary app for the selected login. The other two are standard code app and yubikey.
This is also how I read the meme. Codes are fine, tokens are fine. Your proprietary spyware app is NOT fine (Microsoft) and I hope you get fucked.
Microsoft login works just fine with any TOTP app, like Aegis. They just heavily push you toward their app.
Unless your company doesn't know wtf they're doing and it just doesn't work.
Depends on how it's configured by the company. I've faced in the past the situation of having to login with the company email to be able to use the MFA with a propietary app, which meant I needed to enroll into the BYOD policy and it includes remote device management.
Ended up installing an emulator in the work laptop just for that purpose and left the company shortly after.
It's usually duo. I hate duo so much
MS is fine, your average bank or broker institution though... when it's not SMS, chances are it's an "in-house" solution
You talking about MS authenticator? In what way is that proprietary or spyware?
They offer other options for Microsoft accounts. Using it as a normal TOTP app is the same as any other Authenticator app.
It’s most likely the number matching requirement that the other person doesn’t like, or their employer has a policy that’s annoying.
Not the OP, but I have to use the stupid Microsoft authenticator for work, and half the time it's hibernated and doesn't wake up when prompted, and when I manually open the "verify login" tab, it spits out an OTP but doesn't recheck for that 2 digit number number I have to enter.
And the login prompt on Windows doesn't have a "resend" button, I can merely click "I don't have access to the authenticator app", and then it offers me the option to... Enter a manual code (courtesy of the authenticator app) or use the authenticator app. Dumb as fuck.
If then I opt for the authenticator app instead of the override code, there's a ~30% chance the app will not accept the new number because it's still expecting the former one, if you're too quick to enter it.
Piece of garbage.
Ah. Thanks
Yeah, I've seen that prompt at least 50 times by now. There's almost always a button to use a different authenticator app, which shifts the code to be TOTP compliant.
I don't think I've ever seen that button not be there.
To be fair, the MS authenticator app is also useful as a totp app, so it's not all bad. I mean, I don't use it, but it's not all bad.
If your company (assuming this is for ms365) can also enable FIDO2, so yubikeys are also possible, but they're not enabled by default, so your 365 admin needs to go press a button to allow that for you. MS even supports passkey for passwordless login. But again, not enabled by default. Fun fact: Windows 10/11 also support all of this but if you're on an active directory domain.... You guessed it, it's not enabled by default.
To their credit, Microsoft has made some pretty significant strides in account security in recent years. It's pretty impressive; though requiring a TPM for desktop Windows (especially the "home" versions) still makes me raise an eyebrow. Overall it should help with security.... But a hard requirement? Okay Microsoft. If you say so.
I was reading it as "it never fucking works right" LMAO
I already have an authenticator app. If some service wants to force me to install their own app for their login, they are indeed welcome to fuck off.
Standard authenticator (software or hardware) are, well, standard. You can pick anything compliant and use it with any compliant service. Requiring a specific app means that you have to install yet another app, which may or may not be well made, and may or may not snoop on you, and usually will only work with one service, assuming you have a compatible device to run it to begin with.
It's more than an inconvenience; not insurmountable, but way more work than just having a standard thing that works perfectly well and is based on known and proven algorithms.
Don't forget the dark pattern, where they need to allow push notifications to get two factor to work, but those same push notifications are now used to badger the user and create more advertisement touch points
I can try:
You see, a lot of really smart people worked very hard to make standardized multifactor authentication so different companies can make products that work with the MFA on different sites and services.
The standardized versions are very cross compatible and very very secure.
Some dumb dumbs want to be different and make you install some application on your smartphone so that you can do the exact same thing but only for their site/service. This is widely considered a bad idea, and it makes people sad. Having to install yet another app, just so you can do something that could, and should be possible with the very good existing technology that's been created by those very smart people I mentioned before, is stupid, inconvenient, and frustrating for anyone who understands how these things work, and how secure they actually are.
Since the app that the dumb dumbs made was created by them, for them, and they don't share how that app functions, it can very justly cause concern with those that enjoy their privacy, since the app could be doing any number of potentially nefarious things. When you compare that with the known and trusted methods of authentication created by the smart people, it's understandable that people would not appreciate having to use some proprietary application to do something that's already able to be done in a safe and predictable way.
.... I think I may have used too many big words. You did ask me to eli5....