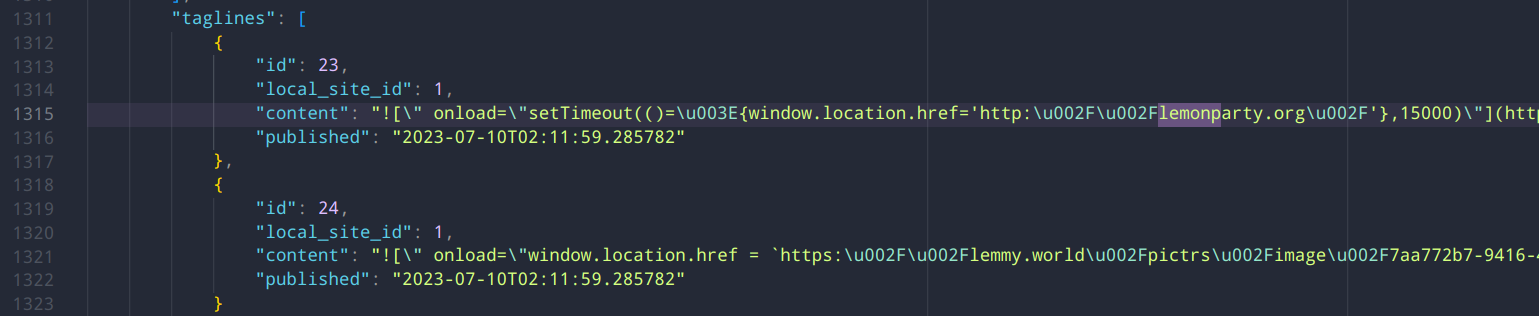
Yea, I switched to this alt. It appears to be one of the assistant admins accts. Seems like an old fashioned anon prank, to me, they're mainly just trying to make stuff offensive and redirect people to lemonparty.
So, y'know, old school.
I don't know if any data is actually in danger, but I doubt it. I don't see why assistant admins would need access to it.