In recent months, we’ve seen an increase in the use of Windows Packet Divert drivers to intercept and modify network traffic in Windows systems. This technology is used in various utilities, including ones for bypassing blocks and restrictions of access to resources worldwide. Over the past six months, our systems have logged more than 2.4 million detections of such drivers on user devices.
The growing popularity of tools using Windows Packet Divert has attracted cybercriminals. They started distributing malware under the guise of restriction bypass programs and injecting malicious code into existing programs.
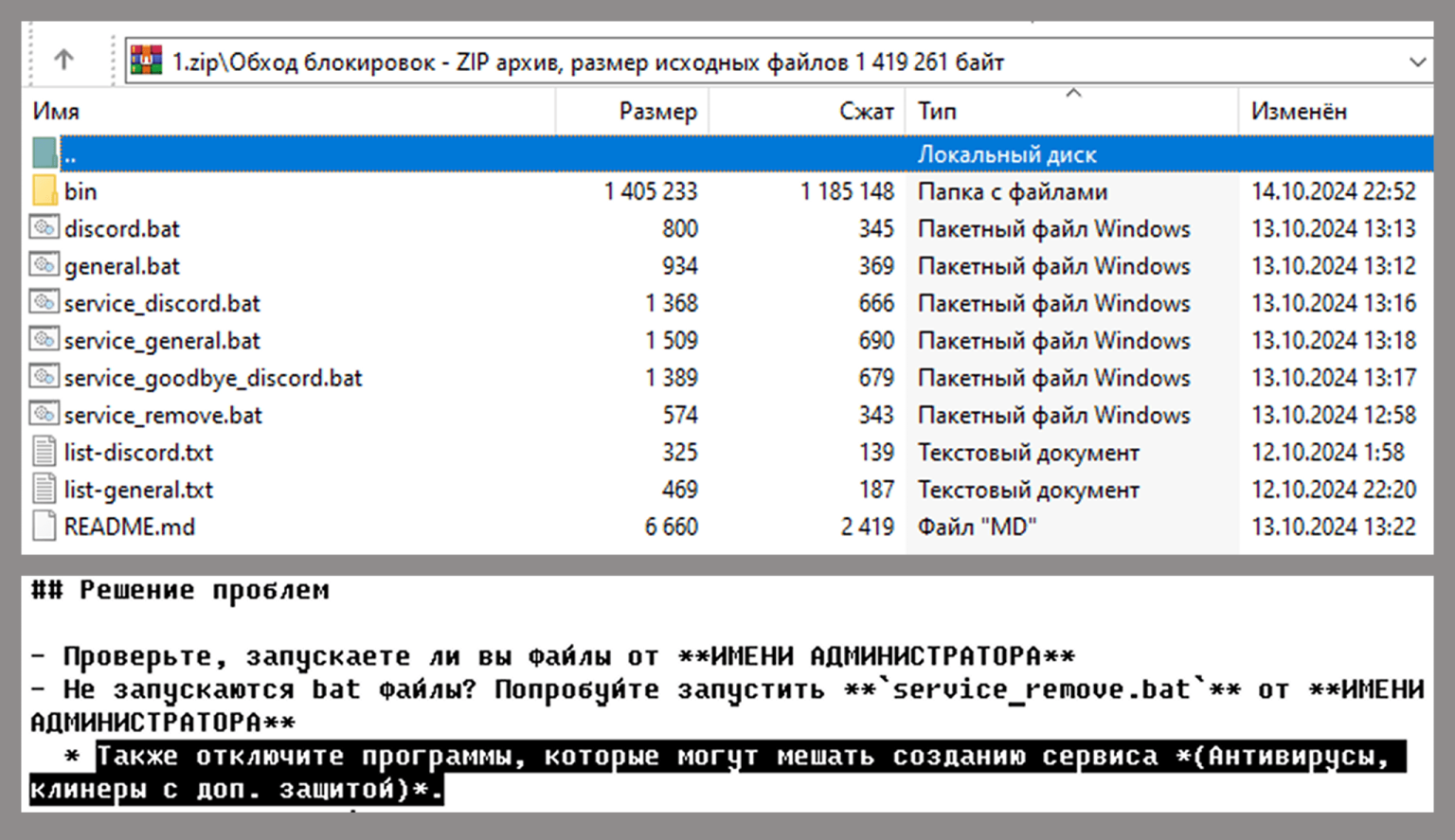
Such software is often distributed in the form of archives with text installation instructions, in which the developers recommend disabling security solutions, citing false positives. This plays into the hands of attackers by allowing them to persist in an unprotected system without the risk of detection. Most active of all have been schemes for distributing popular stealers, remote access tools (RATs), Trojans that provide hidden remote access, and miners that harness computing power to mine cryptocurrency. The most commonly used malware families were NJRat, XWorm, Phemedrone and DCRat.
