this post was submitted on 18 Jul 2023
569 points (100.0% liked)
Technology
58306 readers
3186 users here now
This is a most excellent place for technology news and articles.
Our Rules
- Follow the lemmy.world rules.
- Only tech related content.
- Be excellent to each another!
- Mod approved content bots can post up to 10 articles per day.
- Threads asking for personal tech support may be deleted.
- Politics threads may be removed.
- No memes allowed as posts, OK to post as comments.
- Only approved bots from the list below, to ask if your bot can be added please contact us.
- Check for duplicates before posting, duplicates may be removed
Approved Bots
founded 1 year ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
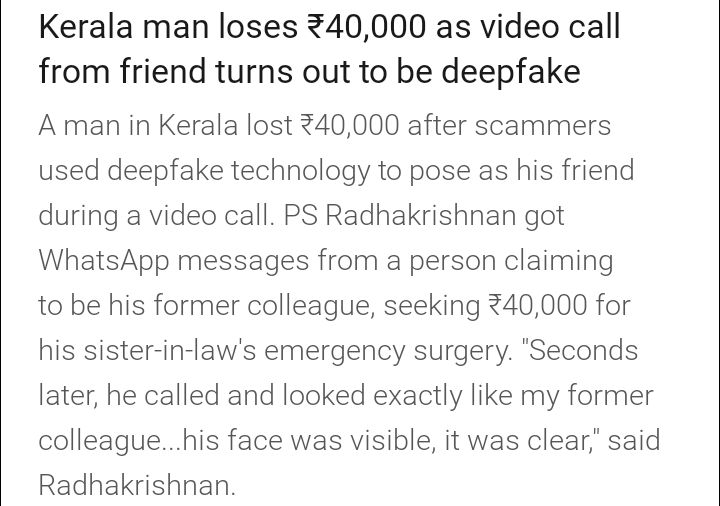
Right now deepfakes doesn't work well when the face is viewed from extreme angles, so you can ask them to slowly turn their face to the side or up/down as far as they can until the face is not visible. It also doesn't work well when something obstruct the face, so ask them to put their hand in their face. It also can't seem to render mouth right if you open it too wide, or stick out your tongue.
I base this from a deepfake app I tried: https://github.com/s0md3v/roop . But as the tech improves, it might be able to handle those cases in the future.
Edit: chance that the scammer use a live deepfake app like this one: https://github.com/iperov/DeepFaceLive . It also supports using the Insight model which only need a single well lit photo to impersonate someone.
or, you know, you can just pickup the phone and call them.
You might not be aware of it, but in India (and SEA), using whatsapp video call is a lot more common than calling using your carrier's phone service. No one would think twice when receiving a whatsapp video calls there.
i am not aware of that, no, but my point is not that the video call itself is suspicious. it is that if you have have a suspicion for whatever reason, normal cell call for a verification is far easier than doing some strange gymnastics the person above suggested (which may or may not work).
I guess that also allows for some 'benefit of the doubt' from the point of view of the victim, it's probably harder to spot artifacts that would be obvious on a TV or monitor screen when the image is v small, and any glitches could be due to the video stream / compression
Two things really:
Unlike in the US, unlimited calls and unlimited sms is not a thing in many countries where WhatsApp is popular. In contrast, WhatsApp calls and messages are free. This was quite significant, especially early on when WhatsApp starting to get popular during the J2ME / Symbian era.
Now that everyone use it, if you don't use it you'll be that one weirdo who don't use WhatsApp and people may choose to not contact you at all (especially if it'll cost money to call you). Even businesses and banks have WhatsApp account these days, so not using WhatsApp will inconvenience you if you live where WhatsApp is dominant.
I had this attack tried on me. It was a video call from my friend's Facebook account. If I didn't know enough to be suspicious, I wouldn't have answered. Luckily I have that friend on Signal, so I knew they wouldn't have called me on Facebook asking for money. I tried calling on Signal, but they didn't answer. They must've not had their phone on them. Calling their home phone worked, though, which is kind of a weird thought.
Their phone was probably offline at the moment.
Nah, they just leave it in another room sometimes and don't care if they miss a call or notification.