news
Welcome to c/news! Please read the Hexbear Code of Conduct and remember... we're all comrades here.
Rules:
-- PLEASE KEEP POST TITLES INFORMATIVE --
-- Overly editorialized titles, particularly if they link to opinion pieces, may get your post removed. --
-- All posts must include a link to their source. Screenshots are fine IF you include the link in the post body. --
-- If you are citing a twitter post as news please include not just the twitter.com in your links but also nitter.net (or another Nitter instance). There is also a Firefox extension that can redirect Twitter links to a Nitter instance: https://addons.mozilla.org/en-US/firefox/addon/libredirect/ or archive them as you would any other reactionary source using e.g. https://archive.today/ . Twitter screenshots still need to be sourced or they will be removed --
-- Mass tagging comm moderators across multiple posts like a broken markov chain bot will result in a comm ban--
-- Repeated consecutive posting of reactionary sources, fake news, misleading / outdated news, false alarms over ghoul deaths, and/or shitposts will result in a comm ban.--
-- Neglecting to use content warnings or NSFW when dealing with disturbing content will be removed until in compliance. Users who are consecutively reported due to failing to use content warnings or NSFW tags when commenting on or posting disturbing content will result in the user being banned. --
-- Using April 1st as an excuse to post fake headlines, like the resurrection of Kissinger while he is still fortunately dead, will result in the poster being thrown in the gamer gulag and be sentenced to play and beat trashy mobile games like 'Raid: Shadow Legends' in order to be rehabilitated back into general society. --
view the rest of the comments
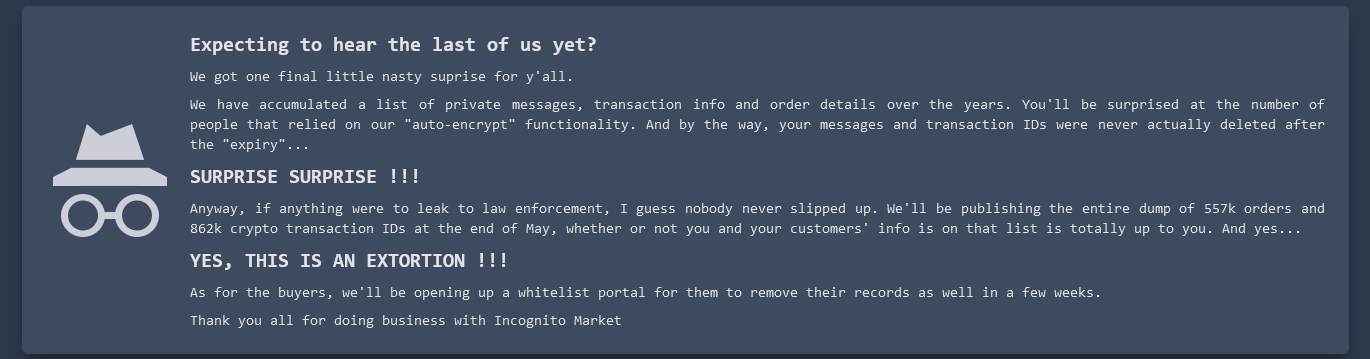
For christs sake:
Only ever explicitly discuss serious illegal activities in person, preferably outdoors and without any technology on you
Only coordinate meetings to discuss the above over an encrypted messaging method such as signal, and in this avoid specifics and keep this to an absolute minimum (metadata can also be incriminating, and phones out computers can be compromised)
If significant payment is involved, cash, barter or work trade are the only acceptable forms. Ever.
Don't be a fucking sucker
Any questions?
you are supposed to PGP encrypt all comms with the seller's public key. The only Incognito customers who will be affected are ones who are stupid and trusted the "auto-encrypt" functionality of a site whose CSS and little fake crypto punks told you it was built by not just ordinary criminals but techbros.
RIP vendors though
You'd use the vendors public key actually, no? Then they would decrypt with the private key? That way they could pass around a key that is not secret
Yes that's correct
ope accidentally a word. Fixed
wouldnt it not even matter due to the blockchain ledger showing transactions?
even if 90% of vendors paid up the last who didnt would have their clients info published and those wallets/transactions will reveal what was bought by those users from other vendors. even just a small fragment opens up a ton of other vendors and users from being exposed
also, lol
Not with monero, the txes aren't traceable down to specific ppl
ah, okay
Buying drugs in person puts someone at risk of violence and death. Buying drugs on a DNM (assuming you use a very basic amount of opsec) the biggest risk is losing a little bit of crypto.
Such an ignorant and privileged thing to say.
And most importantly, buying on the DNM allows you to actually read reviews from other people who purchased from the same vendor. Not on the market itself, but on some of the onion drug forums set up for reviews and discussion. You have the opportunity to check if some vendor's "Heroin" is actually just fentalogues and xylazine. There is no chance to do that IRL unless you're friends with your dealer or something.
This shit is literally life and death for a lot of opioid addicts, and I'm kind of disappointed in Hexbear for this thread labeling everyone caught up in this as just another cryptobro to make fun of. In my experience, neither the vendors nor the customers are using the crypto for any reason other than to facilitate the sales without exposing anything about their identities.
I couldn't agree more. About the importance of being able to read reviews of the vendors made by the community and how much of a boon that is for buyers and their well being, something that simply doesn't exist when it comes to buying from irl dealers. But also about how disappointing it is that so many hexbears not only don't understand this but are being really demeaning towards people who don't deserve it.
The whole "no investigation, no right to speak" thing doesn't just apply to the discussion of politics. And some of the attitudes here about people who use DNMs are almost bordering on victim-blaming. You're right, the ubiquitous use of cryptocurrency on the DNMs is not because the people who use them are the cryptobros we all know and hate, it's because that's literally the only safe way for any of this to work. Most people using the DNMs would rather not have to go through the hassle of having to learn to use crypto in the first place, or deal with the small loss of funds every time they convert their real money into it, or risk losing it because they messed up somehow with their wallet address or something. The use of crypto in this case is an unfortunate necessity most would avoid if they could.
I agree with what you are saying regarding buying drugs online being objectively safer but come on now regarding calling somebody privileged for not wanting to take the other risks associated with buying drugs a different way
"Don't be a fucking sucker. Any questions?" is what the other person said about people who choose to/have to buy their drugs online. I am calling that statement privileged. That person is the one singling out a specific way of getting drugs and demeaning it, not me. Not sure why you'd get on me about something that I'm not only not doing, but actually calling out someone else for doing.
Oh I’m sorry I think I was just tired and misinterpreted the conversation
The risk I'm more concerned about is the risk of cops accessing info and of felony charges.
The risk of cops busting a buyer (of personal use amounts, or even enough for a couple friends) is almost nil for the DNMs because of the amount of work necessary, but a buyer's odds of getting caught during an in-person deal go up drastically because even if they're just after the dealer, the buyer usually gets fucked too since they're right there and part of the bust. The risk of cops busting a dealer/vendor depends a lot on the volume they move, whether it's online or in person. With good opsec the risk is still much lower for vendors than it is for dealers in person. There's also no risk of getting jumped and beaten/killed while you're making a transaction.
Unfortunately, nearly all sellers keep records of their customers and there isn't anything you can do about it. Your number is in your IRL plug's phone and the cops will seize it. The cops may raid your DNM vendor's house while he's using the computer and has everything decrypted. With thoughtful market design you can ensure that only the seller has your info, so that this risk is no higher than for IRL transactions with no third party. But it'll never be 0
Lmao You're automatically risking violence with the police by trying to buy illegal drugs. Using cryptography as cover doesn't change that
If you're buying drugs period "you're automatically risking violence with the police." Full stop. Hell, you're automatically risking violence with the police by existing as a person of color. None of that changes the fact that in-person drug deals are inherently more risky than DNM deals. "lmao"
Also, using encryption "as cover" makes all the difference here. It's massively consequential as this news story makes obvious. The person you're responding to is just being obtuse.
Signal is not secure, nor is Tor. Read "Surveillance Valley". That being said, you probably won't be visited by the cops over a buying a gram of something online.
I'm reading Surveillance Valley, and I'm not sure what you mean by "not secure"
The book states that Signal and Tor were developed by feds, meaning they're completely compromised. It's in the latter chapters.
The fact that tor was developed by feds (CIA agents actually use it in the field, too, IIRC) does not mean it's compromised. Its source code might be among the most audited ones around, including by well-known cryptographers. When the NSA put a backdoor in Dual_EC_DRBG, it was identified quickly and outside of shitty security appliances from RSA in corporate environments, very few projects actually ended up using it. I suspect such a thing would happen with tor.
SELinux is similar: developed by the NSA, but also audited to shit by countless security researcher eager to put their names on the map.
Also, the fact that all tor services that were taken down by LE thus far we know of were taken down through human error on the operator's side or active exploitation of software flaws in the service itself, combined with the Snowden leaks describing tor as a constant pain in their backside, also point towards the same conclusion.
Any specific evidence of compromise? Governments have been known to fund and even directly develop tools later used against them.
I don't have the book checked out anymore, but once you get to the part about Ross ulbrecht, it's right around there. At bare minimum, you can force someone's identity. 0day exploits have also been given to the intelligence services first.
Thanks for the recommendation, I'll read that when I get a chance
What are better alternatives?
I have doubts about there being any.