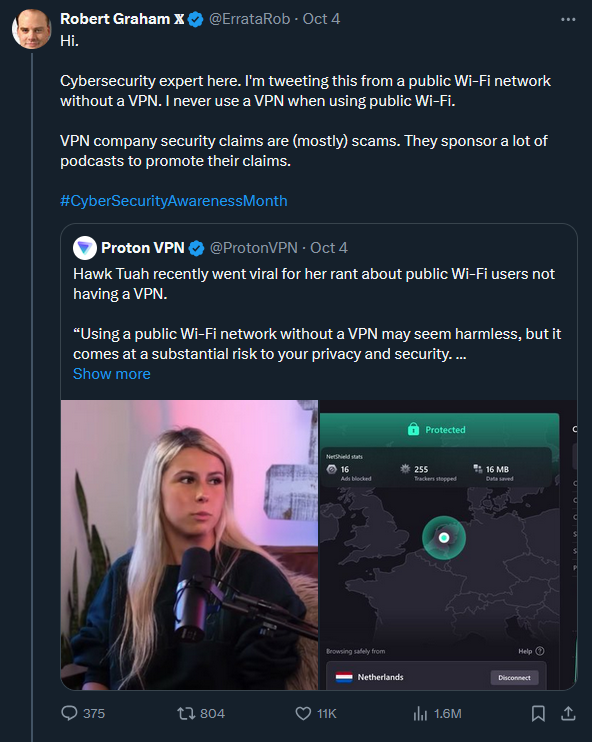
What is he talking about, public WiFi can easily poison and monitor your DNS requests (most people don't know or use encrypted DNS), and there's still tons of non-https traffic leaks all over the place that are plain text. Even if encrypted, there's still deep packet inspection. VPNs can mitigate DPI techniques and shift the trust from an easily snoopable public WiFi to the VPN's more trustworthy exit servers.
This guy really needs to elaborate on what he's trying to say when the cyber security field very much disagrees with this stance. I'm not a huge fan of Proton, but they aren't doing anything wrong here. You should use it for public Wi-Fi.